Saturday, July 30, 2011
Tuesday, July 26, 2011
eHow
eHow is a website where "authors" post articles that are supposedly "how-to"s. In many cases the information so presented is inaccurate. This is not to say that there is not good information there, just that it is of no authority and exists mainly for the promotion of the owners of the website.
If you are really interested in unlocking your Insyde BIOS
One of eHow's authors:
- Using the Incycle H2O CD
- Content Farms
- Social Engineering
- The Internet seems to some as one gigantic Business Opportunity
- What I see as scams
If you are really interested in unlocking your Insyde BIOS
One of eHow's authors:
Friday, July 22, 2011
Google Instant Previews
Google Instant Previews were introduced by Google to their SERPs in 2010/2011.
Wednesday, July 20, 2011
Ray Padgett
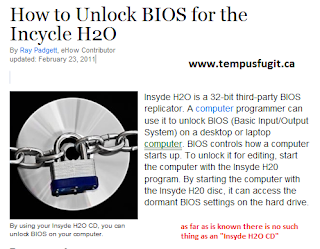
If you write factually incorrect articles for eHow then you deserve a page of your own.
Ray Padgett is not a techology expert. He has a degree in religion and has only been writing nonesence about technology since graduating 2 years ago.
Ray is the author of an article that Internet users will find if they search for methods to unlock Insyde H2O BIOS. The article is a work of fiction and quotes tempusfugit.ca as a source of information.
A visitor to this site asked if I could supply them with a copy of the Insyde H2O CD that Ray had written about on eHow. As I knew that this had never existed I suggested that the visitor contact Ray directly as he was the author of the article.
After some time Ray replied to the visitors request for information on how he could obtain the H2O CD:
This is Ray's reply............
Ray Padgett is not a techology expert. He has a degree in religion and has only been writing nonesence about technology since graduating 2 years ago.
Ray is the author of an article that Internet users will find if they search for methods to unlock Insyde H2O BIOS. The article is a work of fiction and quotes tempusfugit.ca as a source of information.
A visitor to this site asked if I could supply them with a copy of the Insyde H2O CD that Ray had written about on eHow. As I knew that this had never existed I suggested that the visitor contact Ray directly as he was the author of the article.
After some time Ray replied to the visitors request for information on how he could obtain the H2O CD:
This is Ray's reply............
Sorry for the delay, been meaning to reply to you. Unfortunately, that article was written over three years ago. I guess they don't make those CDs anymore. Best of luck finding what you need! Ray
Ray's article was written less than 3 years previously and Ray had never used such a CD as it had never existed!
If Ray's short bio on the eHow page and also on his own website "Cover Me" is to believed, Ray has only been writing since 2009
and that is only 2 years ago (Winter 2011/2012)
Oracle - CRM and MySQL
In my transfer of posts from tempusfugit.ca of topics on CRM, database management systems (SAP, Informix, MySQL etc) this is a holding place for Oracle
Monday, July 18, 2011
HTML5 will this mean the end of Flash?
As more and more take HTML5 on board the need for Flash is getting less and less important. Apple have realized this a long time ago by not bothering with Flash support on some of their products.
There is much copy (Summer 2011) on the fact that web developers need to learn HTML5, I contend that this is not the case unless you indend to develop complex media intensive websites. If you are intending to develop web sites that use the new features that HTML 5 introduces it is more likely that you are going to be using a web development IDE and that will take care of it for you.
There is much copy (Summer 2011) on the fact that web developers need to learn HTML5, I contend that this is not the case unless you indend to develop complex media intensive websites. If you are intending to develop web sites that use the new features that HTML 5 introduces it is more likely that you are going to be using a web development IDE and that will take care of it for you.
Friday, July 15, 2011
ABAP4 - the programing language for R/3
This could be a thing of the past (2012) as SAP may have moved on from this archaic programming environment.
Thursday, July 14, 2011
Wednesday, July 13, 2011
Schadenfreude
Schadenfreude - pleasure taken from someone else's misfortune
This is a term that seems to be a popular one that describes the morbid reaction that some people have towards the rich and famous when they have things not gone their way.
It might be just human nature - but those who are good at something or have achieved some measure of notoriety seem to be held to a higher standard than those that have not managed to be noticed in the crowd.
On the other hand it may just be jealousy or "Tall Poppy" syndrome.
Things that apply to me
I do not deny that there are areas where I take pleasure in seeing that others are having problems with things that I have found "work-arounds" for myself. I say "work-arounds" as they are not "solutions" to problems, they are largely illegal and I believe that it is a case of "not doing as I do".
This is a term that seems to be a popular one that describes the morbid reaction that some people have towards the rich and famous when they have things not gone their way.
It might be just human nature - but those who are good at something or have achieved some measure of notoriety seem to be held to a higher standard than those that have not managed to be noticed in the crowd.
On the other hand it may just be jealousy or "Tall Poppy" syndrome.
Things that apply to me
I do not deny that there are areas where I take pleasure in seeing that others are having problems with things that I have found "work-arounds" for myself. I say "work-arounds" as they are not "solutions" to problems, they are largely illegal and I believe that it is a case of "not doing as I do".
Friday, July 8, 2011
Hide-My-IP.com
Hide-My-IP.html - I think that this is supposed to be HideMyAss - from a visit to Joshua Sham page
I have made a post for HideMyAss - I might as well finish this one along with pages for IP Look-up services.
I have made a post for HideMyAss - I might as well finish this one along with pages for IP Look-up services.
SERP - Search Engine Results Page
This is generally used with reference to a page returned by a search engine such as Google. I am extending its use to include the page returned in Blogger for searches made within that blog.
As the vendor of the search is the same, i.e. Google, the behavior is likely to have similar characteristics.
The following is from a post on my website: (../techwatch.ca/serp.html)
The term SERP is referred to throughout this site and is a generic term that describes the resultant list generated by all of the various search engines. The format of the lists are all different and some are of more use and informative than others.
As the vendor of the search is the same, i.e. Google, the behavior is likely to have similar characteristics.
The following is from a post on my website: (../techwatch.ca/serp.html)
The term SERP is referred to throughout this site and is a generic term that describes the resultant list generated by all of the various search engines. The format of the lists are all different and some are of more use and informative than others.
- How to look in Google Cache (cache_how_to)
- Google Instant Previews (google_preview)
- About the use of robots.txt (robots)
Wednesday, July 6, 2011
Analyzing web server logs
Every web server has the ability to log the accesses to it. These Server Logs can be used as a diagnostic tool to determine the source and intent of access.
In most cases the access of a web server is to retrieve a resource such as a webpage. In addition requests can be made to determine weaknesses and vulnerabilities in the configuration of the server. These accesses are those made by hackers.
Cross-correlating Google Analytics with observations from server logs
Used with Google Analytics a more complete picture of what and where a visitor was looking for and where he/she went after finding your website.
In addition to the actual IP address (or host) the search-string that the visitor used to make a search will be recorded in the server log. The search engine and other data is also returned in the server log entry. To locate the IP address you can perform a reverse IP Lookup, Google Analytics does this for you.
The advantage of direct inspection of the web server log is that the access will be recorded even though the visitor had been using a method to suppress their information. The easiest way to stop Google Analytics collecting your information is to disable JavaScript in your browser.
In most cases the access of a web server is to retrieve a resource such as a webpage. In addition requests can be made to determine weaknesses and vulnerabilities in the configuration of the server. These accesses are those made by hackers.
Cross-correlating Google Analytics with observations from server logs
Used with Google Analytics a more complete picture of what and where a visitor was looking for and where he/she went after finding your website.
In addition to the actual IP address (or host) the search-string that the visitor used to make a search will be recorded in the server log. The search engine and other data is also returned in the server log entry. To locate the IP address you can perform a reverse IP Lookup, Google Analytics does this for you.
The advantage of direct inspection of the web server log is that the access will be recorded even though the visitor had been using a method to suppress their information. The easiest way to stop Google Analytics collecting your information is to disable JavaScript in your browser.
Canon pages on The Technology Muse
My website, tempusfugit.ca, featured a lot of information on Canon and programming with the Canon SDKs. This is currently in the process of being migrated to this blog.
Here are some of the topics that I have moved so far:
Here are some of the topics that I have moved so far:
Peer Blocking
- All about blocking peers
- All pages relating to downloading from Peer to Peer Networks
- Anti-P2P Organizations
- The relative risks of Torrenting
- BTGuard TorrentPrivacy Review
- Choosing a VPN service
It looks like the word has finally got out that PeerBlock (PG2) does nothing to protect your identity while downloading from P2P networks.
It is either that a lot of people have been sent messages from APOs after they thought they were safe when they were using PeerBlock or it has just hit the news somewhere.
In any case I would would be interested in knowing what the source of all the traffic is at the moment it looks pretty global:
 |
| The visitor map from Google Analytics 6 July 2011 showing visits to my peer blocking page |
Tuesday, July 5, 2011
How your ISP can tell what you are downloading
And, what others can tell what you are torrenting as well.
ARM Processors
ARM - RISC
ARM started out standing for Advanced RISC Machines but is now more a case of Intelletual Property rather than a manufacturer. There seems to be much debate (2012) who owns ARM.
RISC - Reduced Instruction Set Computer(ing) - a much scaled down architecture that we have seen developed to date by Intel and AMD (plus others).
The Apple iPad, at least the first generation, used an ARM-Cortex A9 SOC processor.
There is also much debate (January 2012) about ARM devices and Windows 8 (secure_boot.html)
WOA - Windows on Arm
It is my contention that most of the discussion on this (February 2012) are from those that don't know what ARM is. It would seem that it is just a new buzz word and the next thing to come down the line. There is not even much talk of the fact that ARM based tablets could displace the dominance of Intel in the proessors market place. This is, of course if Intel do not get in on ARM manufacture.
The main reason for ARM is the low power requirements associated with a simpler processor architecture. The re-write of Windows 8 to work on such a platform gives rise to debate on whether Windows 8 will be "Windows" in the same way that previous versions were. The fact that a "Start" button and/or a full desktop interface will be there is probably a secondary issue and the fact that Microsoft are all ready behind the 8 ball when it comes to touch/tablet design and marketing is the main concern.
ARM started out standing for Advanced RISC Machines but is now more a case of Intelletual Property rather than a manufacturer. There seems to be much debate (2012) who owns ARM.
RISC - Reduced Instruction Set Computer(ing) - a much scaled down architecture that we have seen developed to date by Intel and AMD (plus others).
The Apple iPad, at least the first generation, used an ARM-Cortex A9 SOC processor.
There is also much debate (January 2012) about ARM devices and Windows 8 (secure_boot.html)
WOA - Windows on Arm
It is my contention that most of the discussion on this (February 2012) are from those that don't know what ARM is. It would seem that it is just a new buzz word and the next thing to come down the line. There is not even much talk of the fact that ARM based tablets could displace the dominance of Intel in the proessors market place. This is, of course if Intel do not get in on ARM manufacture.
The main reason for ARM is the low power requirements associated with a simpler processor architecture. The re-write of Windows 8 to work on such a platform gives rise to debate on whether Windows 8 will be "Windows" in the same way that previous versions were. The fact that a "Start" button and/or a full desktop interface will be there is probably a secondary issue and the fact that Microsoft are all ready behind the 8 ball when it comes to touch/tablet design and marketing is the main concern.
- Microsoft gets it right with Windows 8 on ARM, and why Apple should be worried - Adrian Kingsley-Hughes ZDNet February 10, 2012
- Five Reasons why Windows 8 will be dead on arrival - Steven J. Vaughan-Nichols | February 6, 2012
- Were Microsoft intimidated into Metro by Google? ms_google.html
- ARM Holdings website
Powerline Networking
Some observations and tips
It is well established that the performance of a powerline network system is dependent on the wiring and extraneous interference that the adapters and signal path encounter. The proximity of an EM producing device is likely to degrade the performance of the powerline adapter to in some cases un-usability.
The marketing of filters to overcome the effects of interference
Apart from a monumental exercise in Social Marketing, Echo Dream Venture do not seem to make sense irrespective of their efforts to appear that they have a solution.
Maybe they do, but the lengths to which they go make one suspicious that they are not just trying to "blind" their potential customers with science.
The diagrams above and below are taken from a pdf that the boys at Eco Dream Venture have posted to the Internet. It is not known what the purpose of this pdf (demo sheet) is. Do they expect potential customers to visit their facility in Petaling Jaya, a suburb of Kuala Lumpur? It is a bit far for me to go! Or is it a promotional tool that they hope will be picked up by an international distributor of their lightning isolators.
Calvin and Leong are founders of Eco Dream Ventures (along with Muhammad Syawalfiza). Paul Chang is the guy that dreampt up the idea of using a Lightning Isolator (surge protector) as a means to improve the performance of powerline networking.
Links:
It is well established that the performance of a powerline network system is dependent on the wiring and extraneous interference that the adapters and signal path encounter. The proximity of an EM producing device is likely to degrade the performance of the powerline adapter to in some cases un-usability.
The marketing of filters to overcome the effects of interference
Apart from a monumental exercise in Social Marketing, Echo Dream Venture do not seem to make sense irrespective of their efforts to appear that they have a solution.
Maybe they do, but the lengths to which they go make one suspicious that they are not just trying to "blind" their potential customers with science.
The diagrams above and below are taken from a pdf that the boys at Eco Dream Venture have posted to the Internet. It is not known what the purpose of this pdf (demo sheet) is. Do they expect potential customers to visit their facility in Petaling Jaya, a suburb of Kuala Lumpur? It is a bit far for me to go! Or is it a promotional tool that they hope will be picked up by an international distributor of their lightning isolators.
 |
| It is not clear here that there is any difference between a PLC-WP1 and a PLC-CLLI |
Calvin and Leong are founders of Eco Dream Ventures (along with Muhammad Syawalfiza). Paul Chang is the guy that dreampt up the idea of using a Lightning Isolator (surge protector) as a means to improve the performance of powerline networking.
Links:
- PLC-CLLI - PowerLine Communications Cal-Lab Lightning Isolator
- Business Ops
- Is Surestreamer a scam?
- Using Facebook to promote a business.
How to find information about yourself on-line
There are many things to look and search for when you are trying to find out what's out there about you. Your name is a start, but there are lots of other things that can connect you to your past and activities. Some of which you would rather have kept out of the way of idle eyes.
The search: "how to look at yourself on internet" - 5 July 2011 - actually hit on narcisufing page but it was an opportunity to update this page.
Also, I am not sure if this was what the searcher was looking for - they may have been looking for a way to upload photos to the Internet so that they could look at them using a web browser?
The following was a step-by-step method that I came up with sometime back (in the days when MySpace and Friendster still were on the radar)
Examples here use Google as the search engine although the tips will apply to all engines. I have been using the pseudonym "Anthony Nagy" for examples of how searches report. A big general tip is to change the "number of results" in "Preferences" to 100 from the default value of 10 (Google) - this makes the searching of the page quicker.
If your name is returned in position 80 something then it is easy to miss! Having the number of results set to 10 will mean that you will be on page 8 of the search list.
All browsers have a search function that allows you to search for specific text on the page you are looking at.
This is particularly useful if the page contains a lot of text and requires you to scroll down to see all of it.
I use Firefox and the search, Ctl-F, displays a search box on the lower status bar and you can easily scan to the next occurrence. Microsoft IE has a similar search.
You could ask for the information to be removed - but this is not always possible.
Web sites are more interested in posting information (you do it for them!). Removal has to be done in a lot of cases by a person at the web-site - that is if you can establish contact with one!
a personal web page (or site) is a good way of countering what is said about you on sites that you have no control. A well constructed Blog is another way.
Some Observations:
If you are young person I wouldn't worry too much about the fact that you have information on the Internet that describes your antics in "rowdy parties and drunken escapades".
We are all young once! and even if you are not we all have to let our hair down once in a while. Also proclaiming your sexual preference on the web is an excellent way of "coming out" and what with the equality laws that exist it will give you the advantage should you be discriminated for that reason. (difficult to prove though!)
A much more important issue is to develop a web presence that promotes you in a positive light. The sooner you start one the more time you will have develop it. Expect to "tune" your profile constantly over time. In these days of the Internet it is going to become more and more important that you can be found on the Internet and it is in your best interest to make that presence a "professional" one.
The search: "how to look at yourself on internet" - 5 July 2011 - actually hit on narcisufing page but it was an opportunity to update this page.
Also, I am not sure if this was what the searcher was looking for - they may have been looking for a way to upload photos to the Internet so that they could look at them using a web browser?
The following was a step-by-step method that I came up with sometime back (in the days when MySpace and Friendster still were on the radar)
Examples here use Google as the search engine although the tips will apply to all engines. I have been using the pseudonym "Anthony Nagy" for examples of how searches report. A big general tip is to change the "number of results" in "Preferences" to 100 from the default value of 10 (Google) - this makes the searching of the page quicker.
- Use ALL the search engines (Google and others) to search for Your Name (for starters) [see tips below]
- Do the same searches using any nicknames or alias's that you may have used.
- Again search for your e-mail address, all of them and even parts of it - try search for just the name before the @ for instance
- Places that you have worked - you name might not be in a main index (of a search engine) but it may appear on the pages of a company.
- Search ALL forums and chat pages that you may have participated on.
- Do a search on all the social networking sites such as:
Orkut - Yahoo 360 - MySpace - Zoominfo.com - Friendster - Facebook - Xanga
If your name is returned in position 80 something then it is easy to miss! Having the number of results set to 10 will mean that you will be on page 8 of the search list.
All browsers have a search function that allows you to search for specific text on the page you are looking at.
This is particularly useful if the page contains a lot of text and requires you to scroll down to see all of it.
I use Firefox and the search, Ctl-F, displays a search box on the lower status bar and you can easily scan to the next occurrence. Microsoft IE has a similar search.
What can you do about things you find and don't like
You could ask for the information to be removed - but this is not always possible.
Web sites are more interested in posting information (you do it for them!). Removal has to be done in a lot of cases by a person at the web-site - that is if you can establish contact with one!
a personal web page (or site) is a good way of countering what is said about you on sites that you have no control. A well constructed Blog is another way.
Some Observations:
If you are young person I wouldn't worry too much about the fact that you have information on the Internet that describes your antics in "rowdy parties and drunken escapades".
We are all young once! and even if you are not we all have to let our hair down once in a while. Also proclaiming your sexual preference on the web is an excellent way of "coming out" and what with the equality laws that exist it will give you the advantage should you be discriminated for that reason. (difficult to prove though!)
A much more important issue is to develop a web presence that promotes you in a positive light. The sooner you start one the more time you will have develop it. Expect to "tune" your profile constantly over time. In these days of the Internet it is going to become more and more important that you can be found on the Internet and it is in your best interest to make that presence a "professional" one.
Making backup copies of Blu-Ray Discs
This is (or will be) a collection of all the posts on The Technology Muse relating to the back-up and copy of BD.
Various techniques have been found to transfer BD content to a computer Hard Drive for ease of use with a Media Centre. The brief here is that although DB players/drives/readers are cheap and readily available they are often quite cumbersome to incorporate into a Media Center. Also, the distribution of digital media is made simpler when all material is stored on a central Media Server and networked to multiple Media PCs on the network.
The use of a BD drive on each media box is not practical (or even necessary) and the copy solution is key to this concept.
Links on this blog that relate to Blu-Ray:
Various techniques have been found to transfer BD content to a computer Hard Drive for ease of use with a Media Centre. The brief here is that although DB players/drives/readers are cheap and readily available they are often quite cumbersome to incorporate into a Media Center. Also, the distribution of digital media is made simpler when all material is stored on a central Media Server and networked to multiple Media PCs on the network.
The use of a BD drive on each media box is not practical (or even necessary) and the copy solution is key to this concept.
Links on this blog that relate to Blu-Ray:
Facebook Social Plugin
This plug-in is used to get you to log in to your Facebook account if you are requesting information from another site.The theory here is that you are not likely to be logged in and it forces you to do so if you want to access the information.
If this is a fake and you do sign into your Facebook account your search may be redirected using the anonym.to service. (see below)
In this case it would also not be too difficult to steal your password. I recommend that you change it if you see the logon below and you suspect that the prompt is a fake:
 |
| Is this a real log-in or a fake? When I saw it logging in took me to antonym.to |
However, if you do have a Facebook account and you still would like to see the information, DO NOT LOG-IN using this pop-up. Instead, close it - open up another browser tab and sign in to your Facebook account from there - then access the information the way you did before as now that you are signed in to Facebook you should not get the pop-up getting you to sign-in and possibly steal your information. If you ARE SIGNED-IN to Facebook and you still see the Facebook Social Plugin dialog, then you KNOW that it is a fake.
The anonym.to service:
 |
| While I was waiting I turned off my computer as I did not know what was going on. |
Monday, July 4, 2011
Seedbox Networks - who do they benefit?
I often see the suggestion that the use of a Seedbox being a safer alternative to downloading from P2P networks, but who does a seedbox benefit?
If you have a lot of illegally downloaded material and you want to "stick it" to the music and movie industry and distribute it to all and sundry, then setting up a seedbox may work for you.
If you are looking for a detection-free way of downloading the latest movies and music it is unlikely you are going to find the material that you are looking for on a privately operated seedbox.
If you have an archive of downloaded media and you are looking for that obscure episode of a TV program or the latest Hollywood blockbuster it is more likely that you will find it on a publicly torrented P2P network.
If you subscribe to a hosted seedbox you will have to pay a monthly fee and be restricted to fixed bandwidth and other limitations.
While these limitations may seem far laxer than those imposed by P2P activity and/or the throttling, bandwidth or other traffic shaping applied by your ISP they are there all the same.
Seeing as the selection of things that you want to download will be far less, this will not be an issue.
Narcisurfing - Looking for yourself on the Internet
Narcisurfing - making an Internet search for yourself
Note: This is an earlier post that featured on my website tempusfugit.ca (circa 2006) some of the links have been added back.
To Narcisurf or Egosurf is to make an Internet search for your own name or references to you and any profile that you may have on you.
Alternate spelling narcissurfing (although - I think that looks messy!)
From Narcissistic, narcissism - narcissus (a plant belonging to the genus Narcissus i.e. a daffodil!) and from Classical Mythology - a youth who fell in love with his own image reflected in a pool.
Latin, from Greek narkissos (influenced by narke-, numbness, from its narcotic properties).
Or it could be the numbness experienced by surfing for yourself while munching on too many daffs!
How Dare I Be So Beautiful?
..... We watch in reverence, as Narcissus is turned to a flower.
A flower?
[Suppers Ready - Foxtrot - Genesis 1972]
I first saw this term used by ABCNews reporter - Tory Johnson in an article on Digital Dirt - March 16th 2006
Link to the: abcnews GMA /Careers/story 1729525
Digital Dirt - the power of the Internet can be turned against you.
Be very careful about what you say in a blog - a web site can be created, that looks legitimate, maybe even professional - the site can contain things about you that you wouldn't want your competitors (or prospective employers) to know.
In fact, you may well be doing things on the Internet that are actually harming yourself!
Set a bookmark (or favourite) to this post and return for tips on how to get your information removed from search engine indexes. Or at least minimize the chances of your information being picked up and used against you!
Why would you want to look for yourself on the Internet?
Because other people are and you want to know what is being said about you!
Be careful what you say about yourself in your own blog. When posting messages and replies to forums and chat pages make sure that you don't use your real name
NEVER post your real e-mail address on a web form or page that you are not VERY familiar with - It WILL be harvested!
Also Known As - "Googling yourself" - "self-Googling", "egosurfing" or Vanity Googling
Not that you need to use Google to search for yourself - all of the major search engines will reveal things about you! If fact if you have found this page using Google - why not try one of the other engines.
It could be said that this web-site was born of this pursuit. NO other techniques have been used to direct you to this site apart from me creating a personal web site and monitoring its access - adjusting the content appropriately .
A personal web page (or site) is a good way of countering what is said about you on sites that you have no control. A well constructed Blog is another way.
Note: This is an earlier post that featured on my website tempusfugit.ca (circa 2006) some of the links have been added back.
To Narcisurf or Egosurf is to make an Internet search for your own name or references to you and any profile that you may have on you.
Alternate spelling narcissurfing (although - I think that looks messy!)
From Narcissistic, narcissism - narcissus (a plant belonging to the genus Narcissus i.e. a daffodil!) and from Classical Mythology - a youth who fell in love with his own image reflected in a pool.
Latin, from Greek narkissos (influenced by narke-, numbness, from its narcotic properties).
Or it could be the numbness experienced by surfing for yourself while munching on too many daffs!
How Dare I Be So Beautiful?
..... We watch in reverence, as Narcissus is turned to a flower.
A flower?
[Suppers Ready - Foxtrot - Genesis 1972]
I first saw this term used by ABCNews reporter - Tory Johnson in an article on Digital Dirt - March 16th 2006
Link to the: abcnews GMA /Careers/story 1729525
Digital Dirt - the power of the Internet can be turned against you.
Be very careful about what you say in a blog - a web site can be created, that looks legitimate, maybe even professional - the site can contain things about you that you wouldn't want your competitors (or prospective employers) to know.
In fact, you may well be doing things on the Internet that are actually harming yourself!
Set a bookmark (or favourite) to this post and return for tips on how to get your information removed from search engine indexes. Or at least minimize the chances of your information being picked up and used against you!
Why would you want to look for yourself on the Internet?
Because other people are and you want to know what is being said about you!
NEVER post your real e-mail address on a web form or page that you are not VERY familiar with - It WILL be harvested!
Also Known As - "Googling yourself" - "self-Googling", "egosurfing" or Vanity Googling
Not that you need to use Google to search for yourself - all of the major search engines will reveal things about you! If fact if you have found this page using Google - why not try one of the other engines.
It could be said that this web-site was born of this pursuit. NO other techniques have been used to direct you to this site apart from me creating a personal web site and monitoring its access - adjusting the content appropriately .
A personal web page (or site) is a good way of countering what is said about you on sites that you have no control. A well constructed Blog is another way.
Subscribe to:
Comments (Atom)