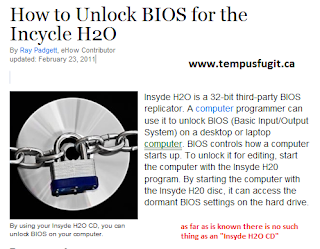
DO NOT download or purchase Camtica 4.3.48970 screen recorder software.
It is promoted by spam emails to owners of blogs by Jiteco. The emails from Deborah Gill offer the author of a blog a free copy of the software in exchange for a review. As such, a review written in response to this request is unlikely to be one that you can take with any authority.
Having received many requests I have decided to write a review - this is it.
It is suspected that Jiteco do not read the blogs that they solicit. If they do then they can comment on this blog posting instead of just sending me offers of evaluation copies of software. If I were to review anything I would purchase it.
Links:
It is promoted by spam emails to owners of blogs by Jiteco. The emails from Deborah Gill offer the author of a blog a free copy of the software in exchange for a review. As such, a review written in response to this request is unlikely to be one that you can take with any authority.
Having received many requests I have decided to write a review - this is it.
It is suspected that Jiteco do not read the blogs that they solicit. If they do then they can comment on this blog posting instead of just sending me offers of evaluation copies of software. If I were to review anything I would purchase it.
Links: